ArsTechnica reports on
a popular distributed denial of service (DDoS) attack that exploits mis-configured DNS servers as traffic amplifiers.
When querying a DNS server, it's trivial to forge the IP address to which the response should be sent. This can be leveraged for nefarious ends.
A DNS server that isn't configured to anticipate this type of attack will easily send a response to the forged IP address that's ten times larger than the request. Hence, this is called a DNS amplification attack. The attacker only needs to send 20 bytes to your server and your server sends 200 bytes to the victim IP.
I am familiar with this because my own Windows DNS servers were attacked.
My DNS servers are authoritative for the domains I operate, but they are not forwarding servers. That is, they won't help you resolve
google.com or
microsoft.com. But they
will resolve
tsotech.com and
btforce.com.
The mistake I made in configuring them was assuming I followed all of the best practices by simply disabling forwarding. That's important, of course, and you should do it if your servers are authoritative and Internet-facing.
It's easy: just check the box shown below in the Properties dialog. These instructions assume you're using Windows Server 2008 R2, but other Windows Server versions should be similar.
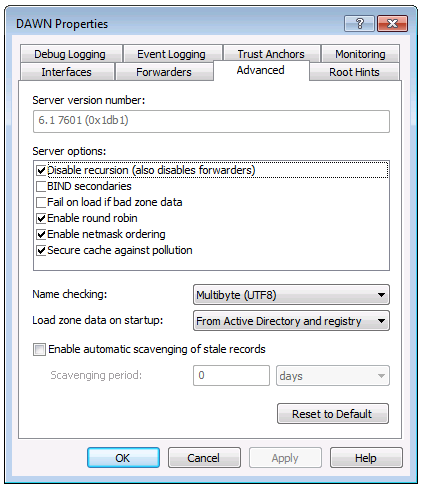
Even with that checked, my servers were seeing surprisingly heavy network utilization, and
dns.exe was responsible. You can determine which processes are responsible for network traffic by opening Resource Monitor (which you can find via Administration Tools > Performance Monitor).
If your server is being attacked, you'll see dns.exe dishing out a ton of sent bytes per second. (The screenshot below shows DNS running normally and not being attacked.)
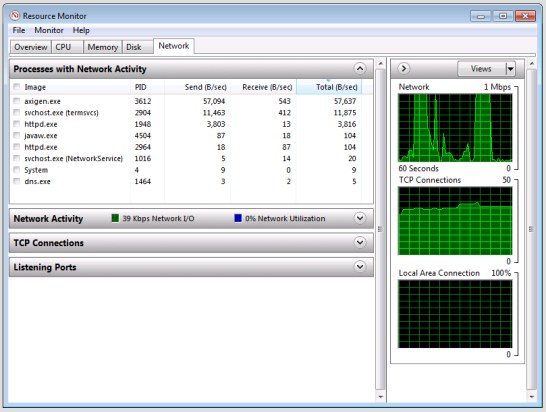
The attack doesn't just leverage your forwarders (or lack thereof). It relies on the fact that even without forwarding enabled, your server will respond with a big list of the Internet's root DNS servers, as if that list were not easily found elsewhere.
An unsuspecting server:
Oh, you're looking for google.com? Well, I'm not authoritative for that domain, but here's a bunch of root servers that can help you find the correct authoritative server.To neuter the attack, you need to remove your server's knowledge of the root DNS servers. This is fine because your server's DNS
client is using your ISP's resolvers, not the root hints known by your DNS server. So go to the
Root Hints section of the Properties dialog and just remove everything.
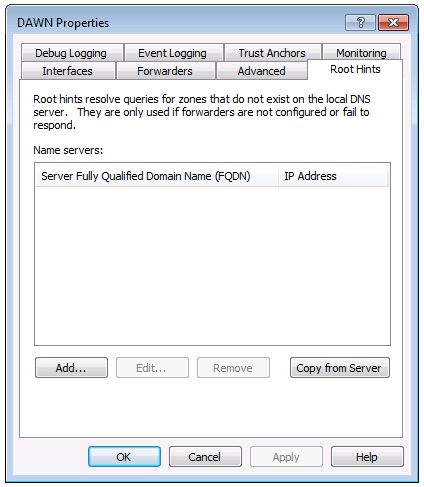
Your DNS server's response to "Resolve google.com, please!" will be reduced to "Go away."
 Even with that checked, my servers were seeing surprisingly heavy network utilization, and
Even with that checked, my servers were seeing surprisingly heavy network utilization, and  The attack doesn't just leverage your forwarders (or lack thereof). It relies on the fact that even without forwarding enabled, your server will respond with a big list of the Internet's root DNS servers, as if that list were not easily found elsewhere.An unsuspecting server:
The attack doesn't just leverage your forwarders (or lack thereof). It relies on the fact that even without forwarding enabled, your server will respond with a big list of the Internet's root DNS servers, as if that list were not easily found elsewhere.An unsuspecting server: Your DNS server's response to "Resolve google.com, please!" will be reduced to "Go away."
Your DNS server's response to "Resolve google.com, please!" will be reduced to "Go away."